Not ready for a demo?
Join us for a live product tour - available every Thursday at 8am PT/11 am ET
Schedule a demo
.svg)
No, I will lose this chance & potential revenue
x
x



It wasn't a sophisticated zero-day exploit. It wasn't a nation-state attack using cutting-edge malware. In December 2024, Chinese state-sponsored hackers breached the U.S. Treasury Department through something far simpler: a single compromised API key from BeyondTrust, their authentication vendor. With that one exposed credential, attackers bypassed millions of dollars in security investments, remotely accessed Treasury workstations, and exfiltrated unclassified documents from one of America's most sensitive government agencies.
This wasn't an anomaly. It was a symptom of a crisis that GitGuardian's 2025 State of Secrets Sprawl report calls "one of the most significant yet underestimated threats in cybersecurity".

The alarming statistics of secrets sprawl in 2024-2025
The scale of secrets exposure has reached staggering proportions. GitGuardian's analysis of 1.4 billion commits across 69.6 million public repositories in 2024 uncovered a landscape of persistent vulnerability that's only getting worse:
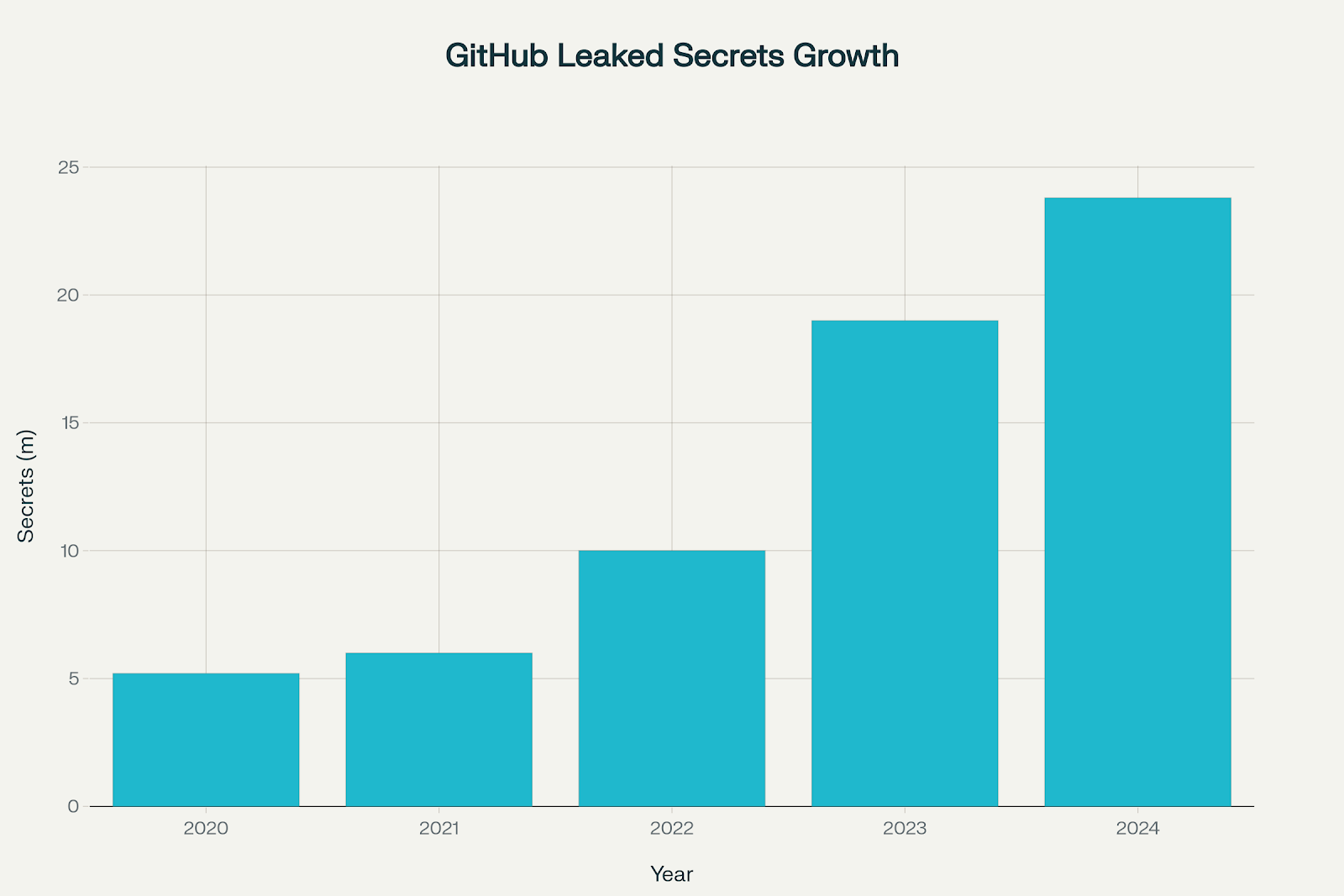
Secrets leaked on public GitHub repositories by year (in millions)
23.8 million secrets were leaked on public GitHub in 2024 alone—a 25% jump from the previous year. But here's what makes this truly terrifying: 70% of secrets leaked in 2022 remain active today, creating an ever-expanding attack surface that compounds over time. These aren't theoretical risks; they're live credentials that attackers can exploit right now.
The problem isn't confined to public repositories. GitGuardian's analysis of private repositories revealed that 35% contain exposed secrets. Worse, sensitive credentials appear five times more frequently in private repositories than public ones—shattering the dangerous assumption that "private equals secure". But the most alarming trend? The tools designed to accelerate development are becoming secret-leakage accelerators.
Here's an uncomfortable truth that many organizations aren't discussing: the tools designed to boost developer productivity may be amplifying security risks. Repositories using GitHub Copilot had a 6.4% secret leakage rate—40% higher than the 4.61% average across all public repositories.
GitHub Copilot usage surged 27% between 2023 and 2024. But researchers at the Chinese University of Hong Kong discovered something troubling: they successfully extracted over 2,700 hardcoded credentials from Copilot, with at least 200 (7.4%) being real, valid secrets that could be traced back to GitHub repositories.
The mechanism is straightforward but alarming. AI coding assistants learn from public code repositories—including code that contains leaked secrets. When developers use prompts that resemble patterns associated with credential storage, these models can inadvertently suggest real credentials from their training data. Security researchers demonstrated this by crafting prompts designed to "force" the model to emit memorized secrets, and it worked.
This doesn't mean abandoning AI coding tools. But it does mean organizations need stronger secret detection controls precisely because AI assistance is becoming ubiquitous.
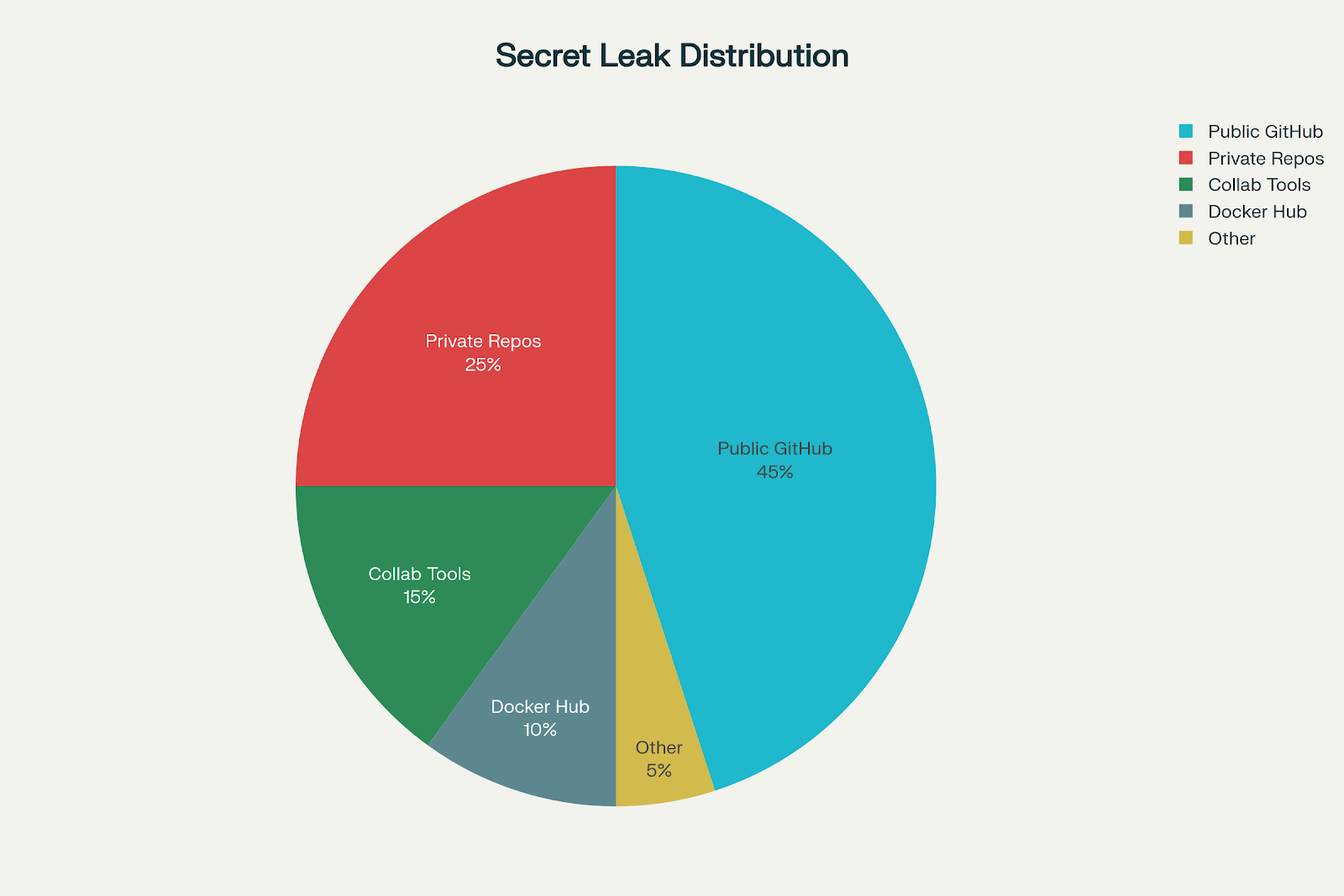
Distribution of secrets exposure across the software development lifecycle
The problem extends far beyond source code repositories. Secrets now sprawl across the entire software development lifecycle, often hiding in places where security teams have limited visibility:
38% of incidents in collaboration tools (Slack, Jira, Confluence) are classified as highly critical or urgent—higher than the 31% in source control management systems. Specifically:
GitGuardian's largest-scale analysis of 15 million public Docker images uncovered 100,000 valid secrets, including AWS keys and GitHub tokens from Fortune 500 companies. Alarmingly, 98% of detected secrets were found in image layers, with ENV instructions alone accounting for 65% of all secret leaks. And because Docker Hub lacks a partner notification system for secret exposure, these credentials often remain valid indefinitely.
Perhaps most concerning is the false sense of security around private repositories.
AWS IAM keys appear in 8% of private repositories—5x more frequent than public repositories
The Treasury breach wasn't isolated. 2024 saw a cascade of high-profile incidents where leaked credentials served as the initial attack vector:
Attackers gained unauthorized access to Sisense's self-managed GitLab repository, where they found a hardcoded token that granted access to Sisense's Amazon S3 buckets. From there, they exfiltrated terabytes of customer data, including millions of access tokens, email passwords, and SSL certificates. The breach prompted CISA to issue an urgent advisory to all Sisense customers—a reminder that supply chain attacks through exposed credentials can have exponential impact.
An exposed GitHub token gave attackers access to 5,000+ repositories containing 273GB of source code, including the wildly popular Wordle game. GitGuardian's analysis of the leaked data uncovered over 4,000 unique secrets and at least 200 critical secrets lurking in the code. The breach demonstrated how a single exposed credential can unlock an organization's entire intellectual property.
Malware on a CircleCI engineer's laptop compromised a valid, MFA-backed SSO session. Because the engineer had privileges to generate production access tokens, attackers exfiltrated customer environment variables, tokens, and keys from the popular CI/CD platform. CircleCI advised all customers to immediately rotate "any and all secrets"—affecting over a million software engineers worldwide.
After social engineering an employee to accept an MFA push notification, attackers found a PowerShell script containing hardcoded credentials for Uber's Privileged Access Management (PAM) solution—Thycotic. With admin access to the PAM system, they compromised AWS, GCP, Google Drive, Slack, SentinelOne, HackerOne, and internal dashboards. The entire breach pivoted on a single hardcoded credential in a script.
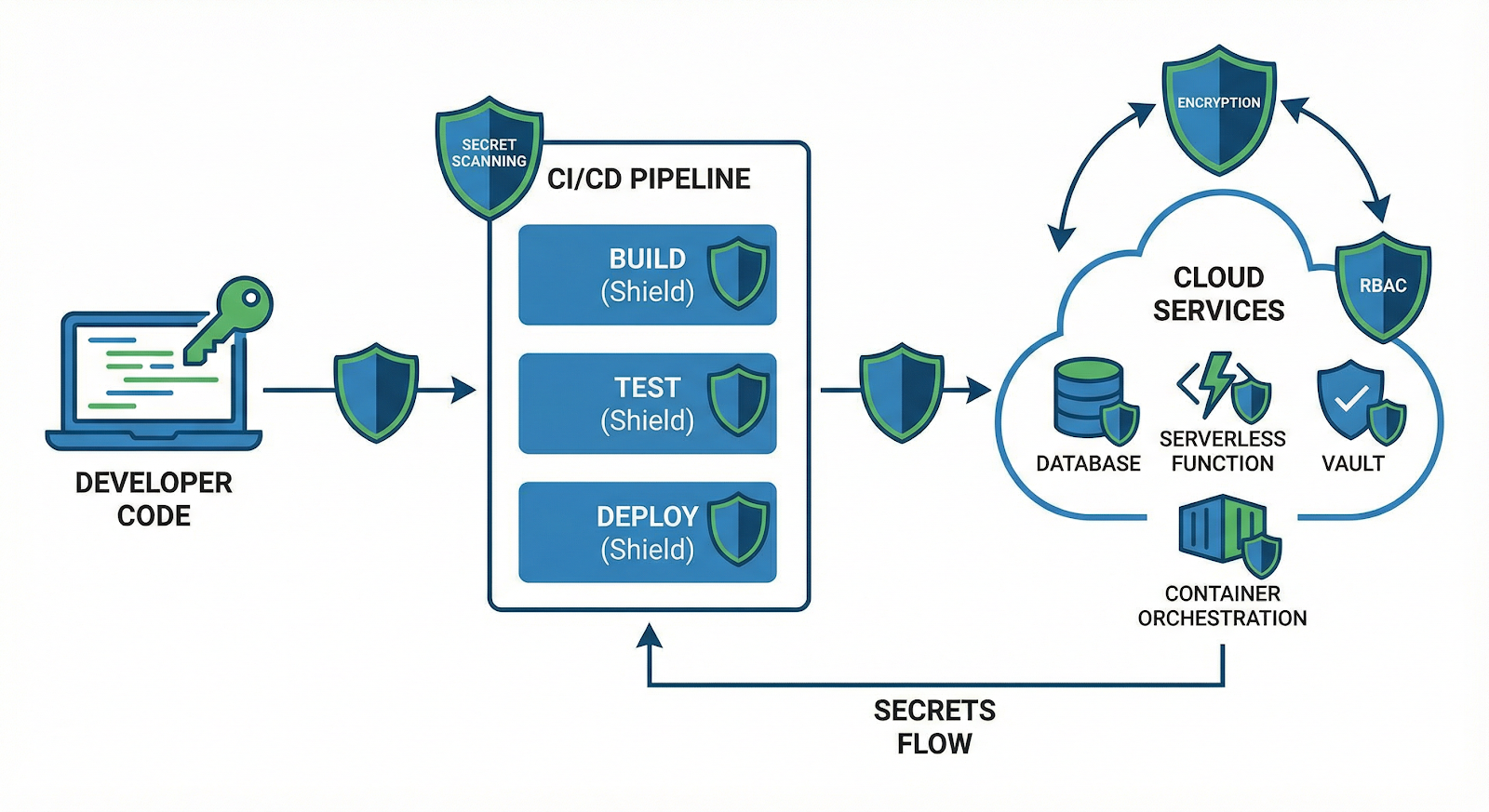
Secrets management architecture across the software development lifecycle
Understanding the threat is step one. Here's how leading organizations are systematically eliminating hardcoded secrets from their distributed systems.
Most enterprises still have credentials scattered across configuration files, environment variables, CI/CD pipelines, and code repositories. The first step toward centralized control is comprehensive migration to managed secret stores.
AWS recently announced managed external secrets—a feature offering default-enabled automatic rotation for third-party SaaS secrets without requiring Lambda function creation.
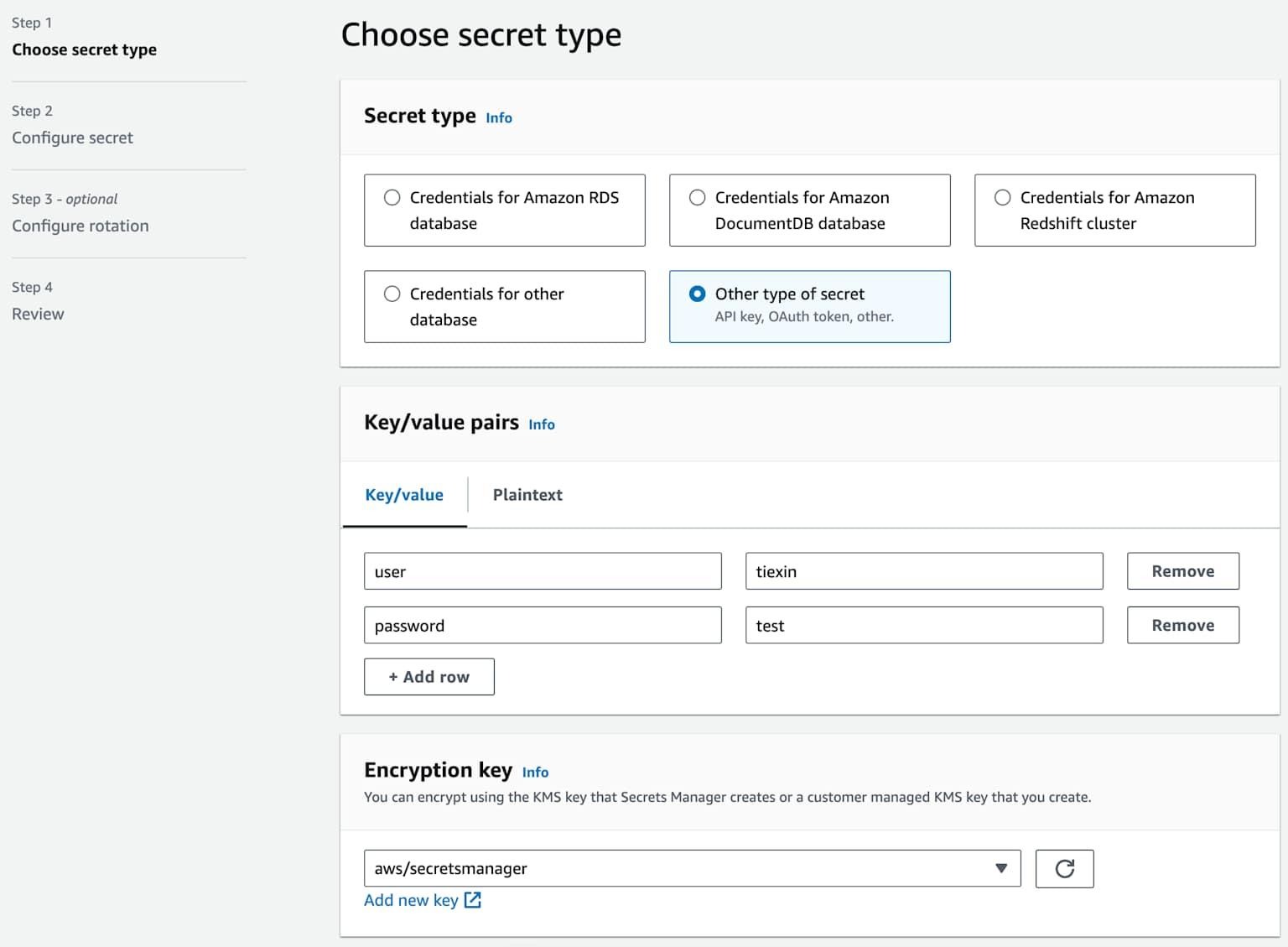
Handling Secrets with AWS Secrets Manager
Vault's database secrets engine generates credentials dynamically based on configured roles, eliminating the need for applications to hardcode credentials. Services "ask" Vault for database credentials, and administrators specify time-to-live (TTL) so credentials are automatically revoked when no longer used.
Dynamic secrets are suited for time-bound workloads like batch jobs or CI/CD executions, while auto-rotated secrets work better for longer-lasting workloads needing stable connections.
Migration Best Practice: AWS recommends a phased approach—integrate with Secrets Manager before cloud migration to simplify the transition, then enable automatic rotation post-migration to immediately address legacy exposure risks.
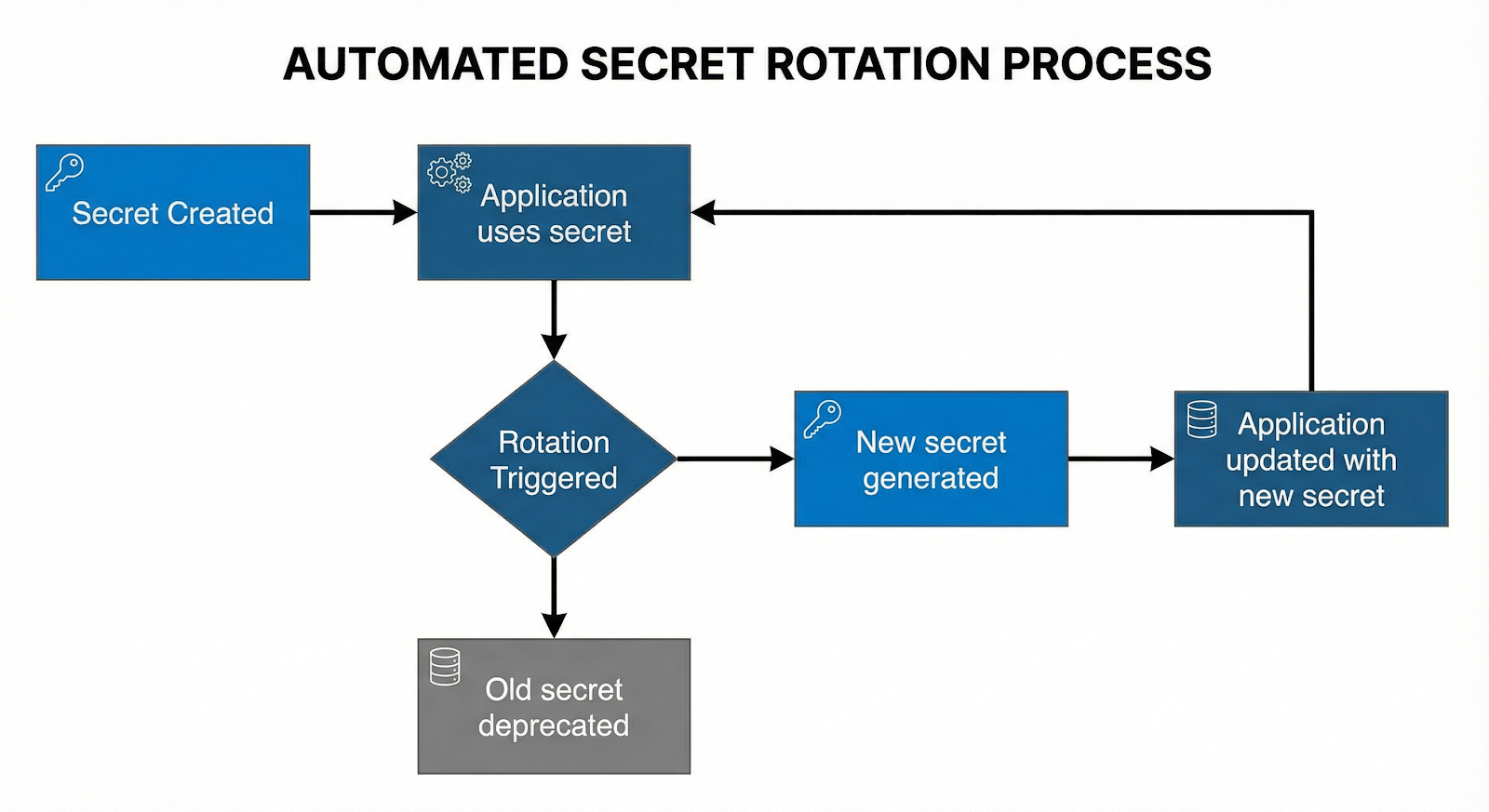
Automated secret rotation workflow for zero-downtime credential management
The most damning statistic isn't the number of leaked secrets—it's that 70% of secrets leaked in 2022 remain active today. Remediation is slow due to enforcement gaps and complex workflows.
AWS provides multiple rotation approaches:
Managed rotation: For supported secrets, AWS configures and manages rotation without Lambda functions
Dynamic credentials offer an even more elegant solution. Instead of rotating static credentials, Vault generates unique, short-lived credentials for each request:
Use environment-specific secrets with mandatory review requirements rather than repository-level secrets
For Kubernetes environments, three approaches have emerged as industry standards:
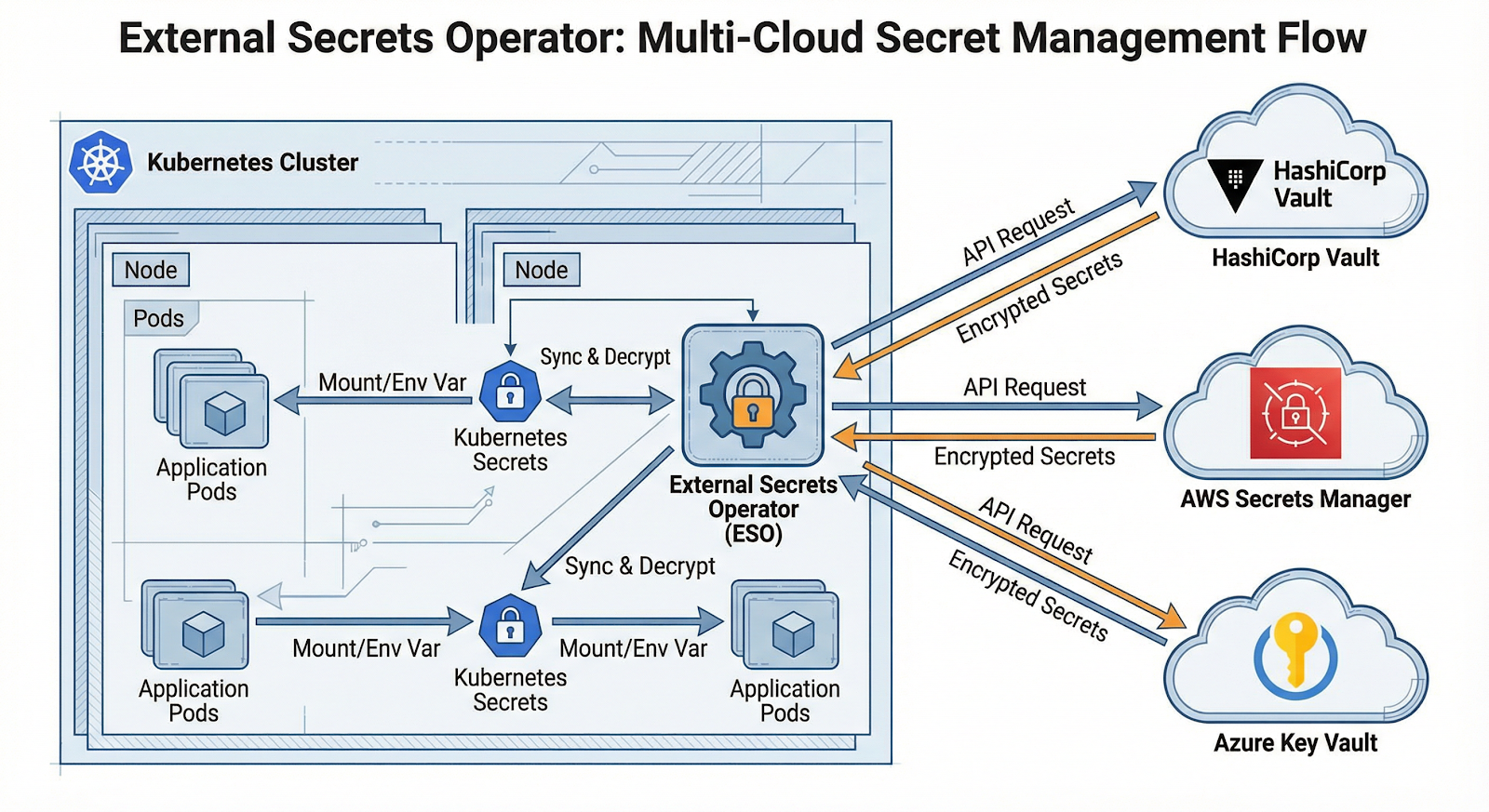
External Secrets Operator unifying multi-cloud secrets management in Kubernetes
GitHub now enables push protection by default for all public repositories, automatically blocking commits when it detects secrets matching 200+ token types from 180+ service providers. The company discovered one million exposed secrets in public repositories in just the first two months of 2024.
However, there's a critical limitation: GitHub Push Protection only detects secrets with standardized patterns. It struggles with generic secrets—hardcoded passwords, database connection strings, custom authentication tokens—which accounted for 58% of all leaked credentials in 2024.
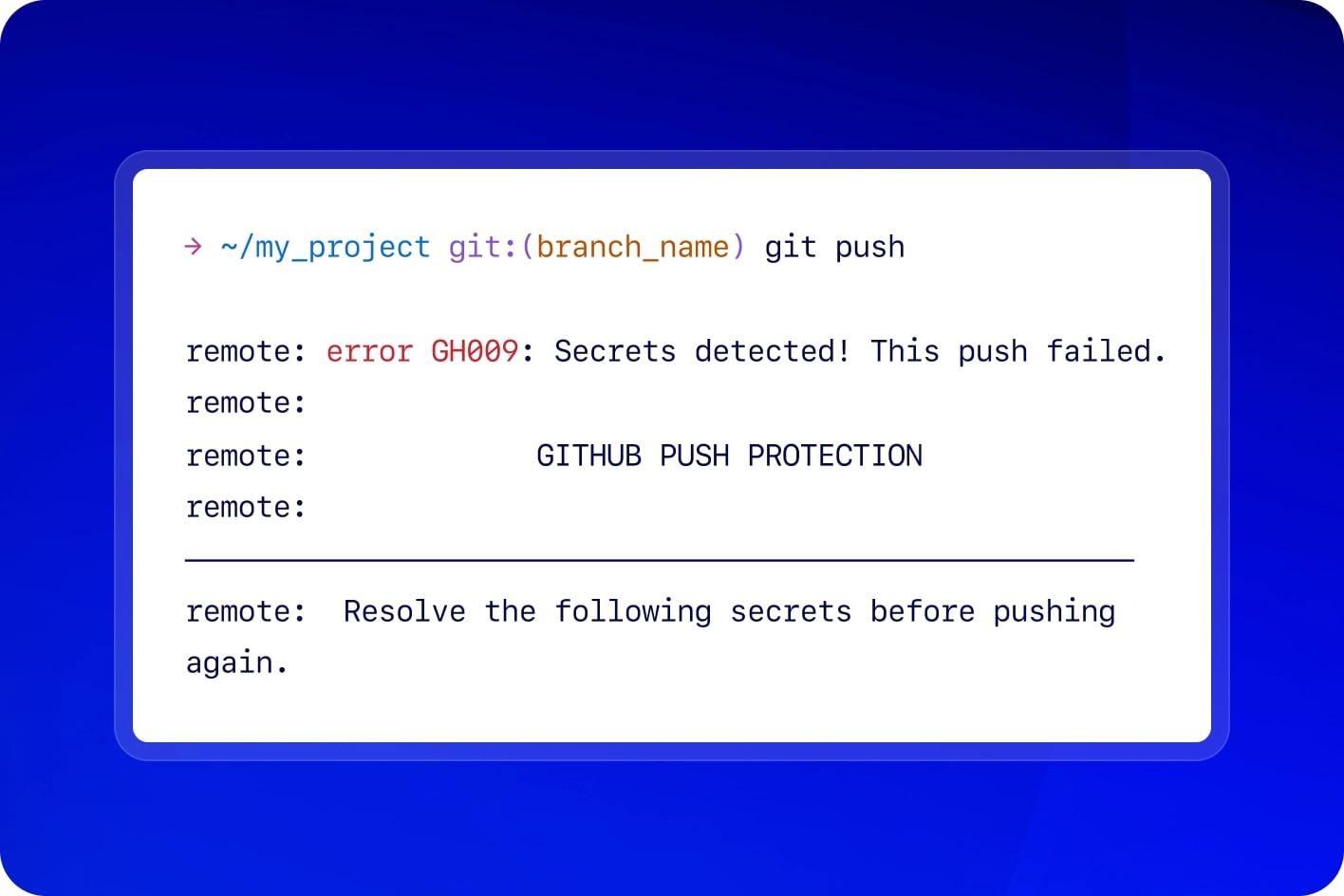
GitHub Secret Protection · GitHub
Pre-commit hooks: Implement tools like GitGuardian's ggshield, TruffleHog, or Gitleaks to scan before code leaves developer machines
The OWASP Secrets Management Cheat Sheet emphasizes a lifecycle approach:
Native Kubernetes secrets are base64-encoded, not encrypted—trivially reversible by anyone with cluster access. They're difficult to manage at scale, have no built-in rotation, and secrets in manifests committed to Git create exposure risks.
ESO provides three core components:
Security tools that disrupt developer workflows face resistance. Modern solutions must balance security with productivity.
1Password Developer Tools exemplify this approach:
The key insight: centralized, encrypted storage across teams with automatic synchronization eliminates the "outdated .env file" problem while providing audit trails for compliance.
The secret sprawl crisis won't solve itself. Every passing day, the 23.8 million secrets leaked in 2024 age into the 70% that remain active years later. Every unrotated credential, every hardcoded password in a private repository, every API key baked into a Docker image represents a potential breach vector waiting to be exploited.
But organizations that implement defense-in-depth for secrets management—centralized stores, automated rotation, multi-layer detection, and developer-friendly tooling—are systematically closing these attack vectors.
The Treasury breach, the Sisense supply chain attack, the New York Times code leak—these weren't sophisticated attacks. They were simple exploitation of exposed credentials. And they're entirely preventable.
The question isn't whether your organization has leaked secrets. The question is whether you'll find them before attackers do.
Understanding the threat is step one. But implementing these strategies requires hands-on experience with the tools and techniques that make secrets management truly effective. This is where many security teams stumble—they know what needs to be done, but lack the practical skills to execute.
AppSecEngineer helps teams bridge this gap with practical training in AWS Secrets Manager, HashiCorp Vault, Kubernetes secrets hardening, and GitOps security for CI/CD pipelines. Our hands-on approach lets engineers experience the consequences of misconfiguration and master the tools that prevent breaches—because when it comes to secrets management, theoretical knowledge without practical experience is as dangerous as having no knowledge at all.
.avif)
Secrets Sprawl is a persistent security crisis characterized by the uncontrolled exposure of sensitive credentials, such as API keys, database passwords, and access tokens, across an organization's entire software development lifecycle. GitGuardian's 2025 report identified it as one of the most significant and underestimated threats, where an ever-expanding attack surface is created as leaked secrets remain active for years.
The scale of secrets exposure is staggering. In 2024, 23.8 million secrets were leaked on public GitHub alone, which was a 25% increase from the previous year. The key long-term risk is that an alarming 70% of secrets leaked in 2022 were still active as of 2024, meaning they compound the attack surface over time, offering attackers live credentials to exploit.
No, the document shatters the dangerous assumption that a private repository equals secure. GitGuardian's analysis found that 35% of private repositories contain exposed secrets. Furthermore, sensitive credentials, like AWS IAM keys, appear five times more frequently in private repositories than in public ones, and hardcoded passwords appear three times more often.
AI coding assistants, such as GitHub Copilot, can inadvertently amplify security risks. Repositories using Copilot had a 6.4% secret leakage rate, which is 40% higher than the average. This paradox occurs because these models learn from public code repositories that contain leaked secrets. When developers use certain prompts, the AI can suggest real, memorized credentials from its training data, effectively leaking valid secrets into new codebases.
Secrets sprawl extends far beyond source code. They are frequently found in: Collaboration Tools: 6.1% of Jira tickets and 2.4% of corporate Slack channels were found to contain leaked secrets, making Jira the most vulnerable collaboration tool. Docker Images: A massive 100,000 valid secrets were uncovered in 15 million public Docker images. 98% of these secrets were found in image layers, with ENV instructions accounting for 65% of the leaks.
Leading organizations follow a defense playbook that includes five key strategies: Migrate to Managed Secret Stores: Centralize credentials using tools like AWS Secrets Manager or HashiCorp Vault. Implement Automated Rotation: Deploy zero-downtime, automated rotation to immediately revoke legacy and compromised credentials. Eliminate Secrets from CI/CD: Use OIDC (OpenID Connect) authentication instead of long-lived tokens for cloud access. Deploy Multi-Layer Detection: Implement scanning at all phases: pre-commit hooks, CI/CD scanning, historical scanning, and container registry scanning. Secure Kubernetes: Utilize the External Secrets Operator (ESO) to sync secrets from managed stores into the cluster, avoiding the insecure native Kubernetes secrets format.
Automated rotation directly addresses the "70% Problem," which is the statistic that 70% of secrets leaked in 2022 remained active two years later. Slow manual remediation is the root cause. Automated rotation, like the dynamic credentials generated by HashiCorp Vault, ensures credentials are short-lived, are automatically revoked after a Time-to-Live (TTL), and minimize the window of opportunity for an attacker to use a compromised secret.
Several high-profile breaches have pivoted on a single exposed credential. For example, in December 2024, Chinese state-sponsored hackers breached the U.S. Treasury Department using one compromised API key. The Uber Breach (September 2022) was caused by a PowerShell script containing hardcoded credentials for their Privileged Access Management solution. The Sisense Supply Chain Attack (April 2024) began with a hardcoded token found in a self-managed GitLab repository.
In April 2024, attackers accessed Sisense's self-managed GitLab repository, where they found a hardcoded token. This token granted them access to Sisense's Amazon S3 buckets, allowing them to exfiltrate terabytes of customer data, including millions of access tokens, email passwords, and SSL certificates. The severity of the breach led CISA to issue an urgent advisory to all Sisense customers.
AWS Secrets Manager is the cloud-native choice, recently offering default-enabled automatic rotation for third-party SaaS secrets. HashiCorp Vault offers multi-cloud flexibility and excels with its dynamic secrets engine, which generates unique, short-lived credentials for each request, automatically revoking them after a specified Time-to-Live (TTL). Vault also supports static credential rotation for longer-lasting workloads.


.png)
.png)

Koushik M.
"Exceptional Hands-On Security Learning Platform"

Varunsainadh K.
"Practical Security Training with Real-World Labs"

Gaël Z.
"A new generation platform showing both attacks and remediations"

Nanak S.
"Best resource to learn for appsec and product security"
.svg)




.svg)



.png)
.png)

Koushik M.
"Exceptional Hands-On Security Learning Platform"

Varunsainadh K.
"Practical Security Training with Real-World Labs"

Gaël Z.
"A new generation platform showing both attacks and remediations"

Nanak S.
"Best resource to learn for appsec and product security"


.svg)
.svg)




United States11166 Fairfax Boulevard, 500, Fairfax, VA 22030
APAC
68 Circular Road, #02-01, 049422, Singapore
For Support write to help@appsecengineer.com



.svg)
