Not ready for a demo?
Join us for a live product tour - available every Thursday at 8am PT/11 am ET
Schedule a demo
.svg)
No, I will lose this chance & potential revenue
x
x


This bug is a case study of a crippling critical severity bug on a multi-billion dollar Organization.
This blog unpacks a sophisticated attack chain that exploits file upload and image processing workflows to exfiltrate AWS temporary credentials via a CDN. By manipulating file extension whitelisting, I was able to upload .odt (OpenDocument Text) files, which were subsequently parsed by LibreOffice on the backend to generate image previews. Leveraging a Server-Side Request Forgery (SSRF) vulnerability during this parsing process, I extracted AWS temporary credentials. These credentials were then stealthily embedded into a PNG image, which was automatically served through the application’s CDN infrastructure.
This blog will walk through the technical steps of bypassing file restrictions, abusing document conversion pipelines, and writing malicious .odt files. Readers will gain insight into the risks posed by chained vulnerabilities in modern web and cloud environments, and learn practical detection and mitigation strategies to safeguard against similar threats.
Tags: SSRF, AWS, File Upload, LibreOffice
File uploads are everywhere—from profile pictures to document previews—but they’re also among the most complex and dangerous surfaces in modern web applications. This is a deep dive into how we found and exploited a file upload feature in a multi-billion dollar SaaS platform (REDACTED) to execute server-side request forgery (SSRF) and ultimately leak temporary AWS credentials.
No fancy payloads. No cross-site scripting. Just a file upload interface, some XML, and an unexpected backend player: LibreOffice.
When applications allow users to upload files, they typically implement validation mechanisms—like MIME type checks, extension whitelists, antivirus scanning, and content inspection. These controls are often good enough to block simple attacks.
But trust begins to erode when an application allows uploading files by URL. This feature, while user-friendly, becomes an instant candidate for Server-Side Request Forgery (SSRF).
SSRF is a vulnerability where an attacker tricks a server into making HTTP requests to internal or protected endpoints. This can result in access to internal admin panels, cloud metadata services, or even other services running on the same network.
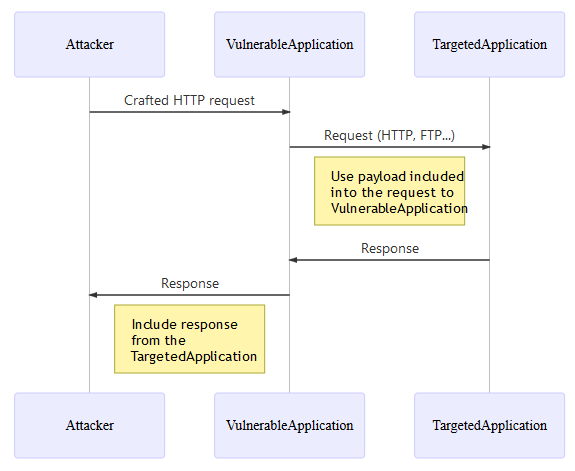
We attempted to upload a file via URL.
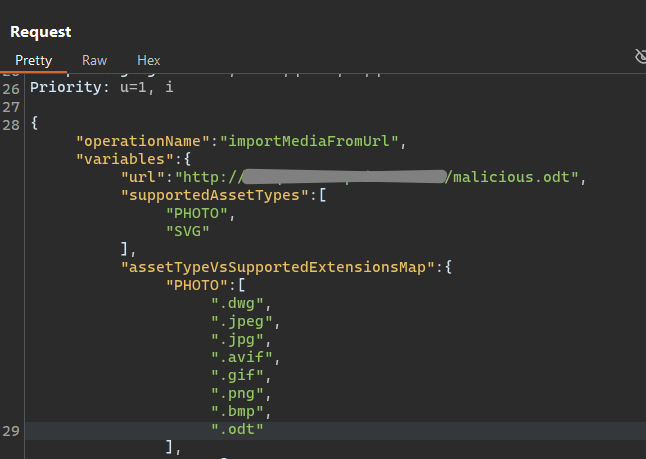
Initially uploading with a URL with an unsupported extension ( the extension of our choice not added in assetTypeVsSupportedExtensionsMap parameter ) would get an "message":"Extension unsupported! Error message.
By modifying the extension whitelist in the request, we were able to upload unsupported files like .html. The server accepted them, and rendered a preview.
So we have,
assetTypeVsSupportedExtensionsMap.That meant something on the backend was:
But what was doing the rendering?
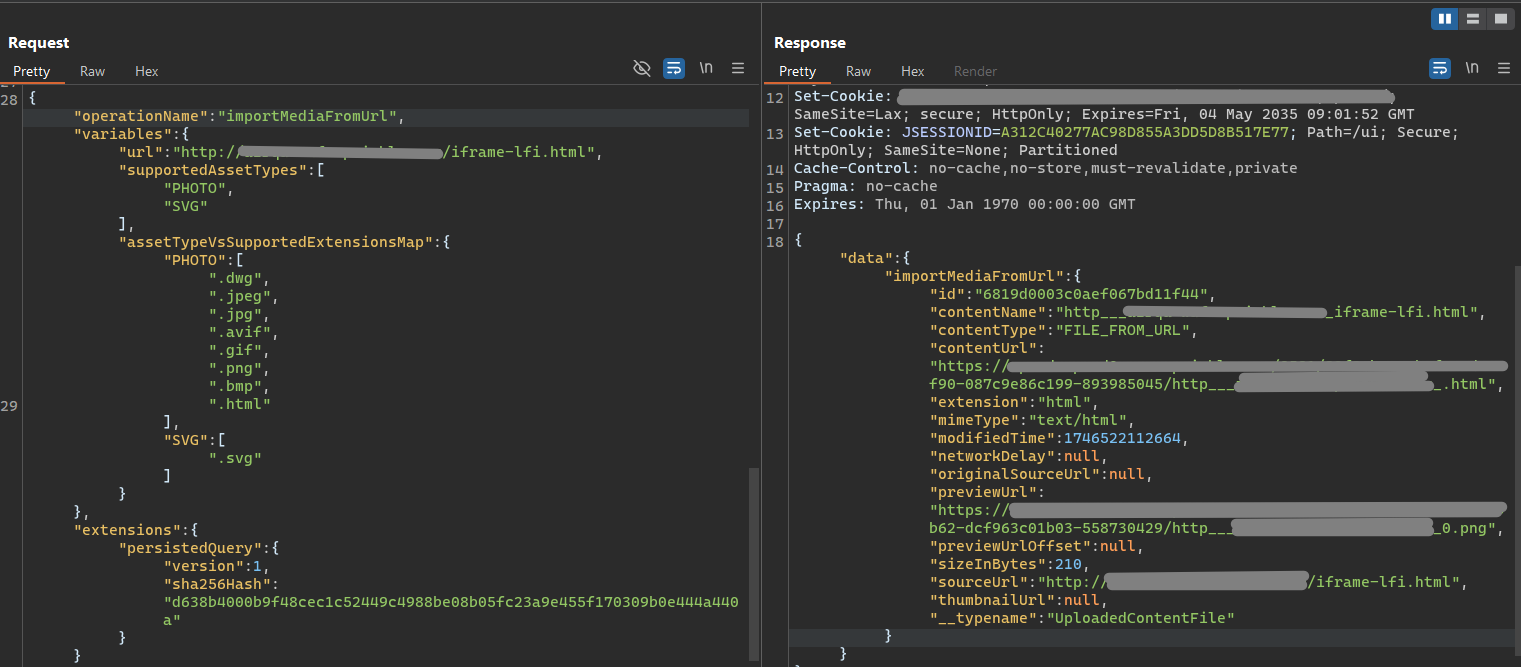
To identify the software generating thumbnails, we needed visibility into how the system handled our uploads. Since the preview image was generated server-side, we couldn't directly observe what happened during rendering. So we tried a pingback technique.
We uploaded an HTML file with a tag that would force any rendering engine to make a request to our server:
If the rendering engine attempted to process this HTML file to generate the preview, it would need to parse this HTML in order to generate the preview thumbnail image, during the parsing process, the backend would hit our server—revealing its identity via headers, especially the User-Agent headers.
We received a request with a User-Agent string revealing that the backend used LibreOffice to process the uploaded documents and generate previews.
Pingback confirms LibreOffice in use at the backend
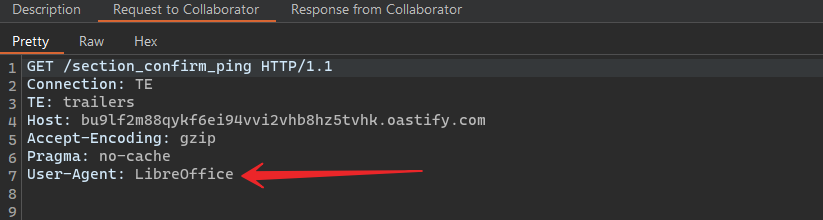
This was a breakthrough.
LibreOffice is an open-source office suite commonly used in server environments for headless document processing—automated conversions, thumbnail generation, PDF exports, etc.
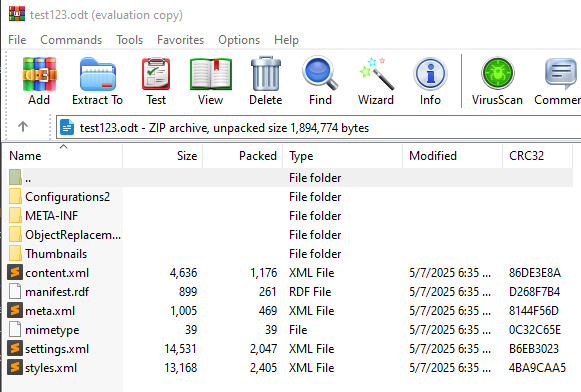
LibreOffice supports parsing complex document types like ODT (OpenDocument Text), which are ZIP archives containing XML files, as seen in the below image. Below is a test .odt file and its contents when uncompressed. You can see it is majorly XML and heavily would rely on a XML parser.
Critically, it also supports dynamic content loading through attributes like xlink:href within its content.xml file.
That means you can create a document that references external resources. When LibreOffice renders it, it will attempt to fetch those resources—even if they point to internal services.
We have an opening now and an action plan. Let’s get to it.
An .odt file contains a file called content.xml, which holds the main body of the document. In it, we embedded the following SSRF payload:
In the backend, This instructs LibreOffice to load the content from the AWS metadata service, which lives at a special internal IP address (169.254.169.254) used by EC2 instances to expose sensitive information—like temporary access keys for IAM roles.
This content, fetched dynamically by the xlink:href would sit within the TextArea block, eventually embedded within the .odt file, eventually making itself the “Face” of the document.
The preview thumbnail generated is more like a picture of the face i.e. the document.
Post this, after we have our payload within content.xml, we need to compress the folder back to the original .odt file and upload it via the URL parameter.
Want to practice this kind of SSRF attack and learn how to defend against it in real-world Java applications?
Try our hands-on course: Attacking and Defending SSRF (Server-Side Request Forgery) with Java EE
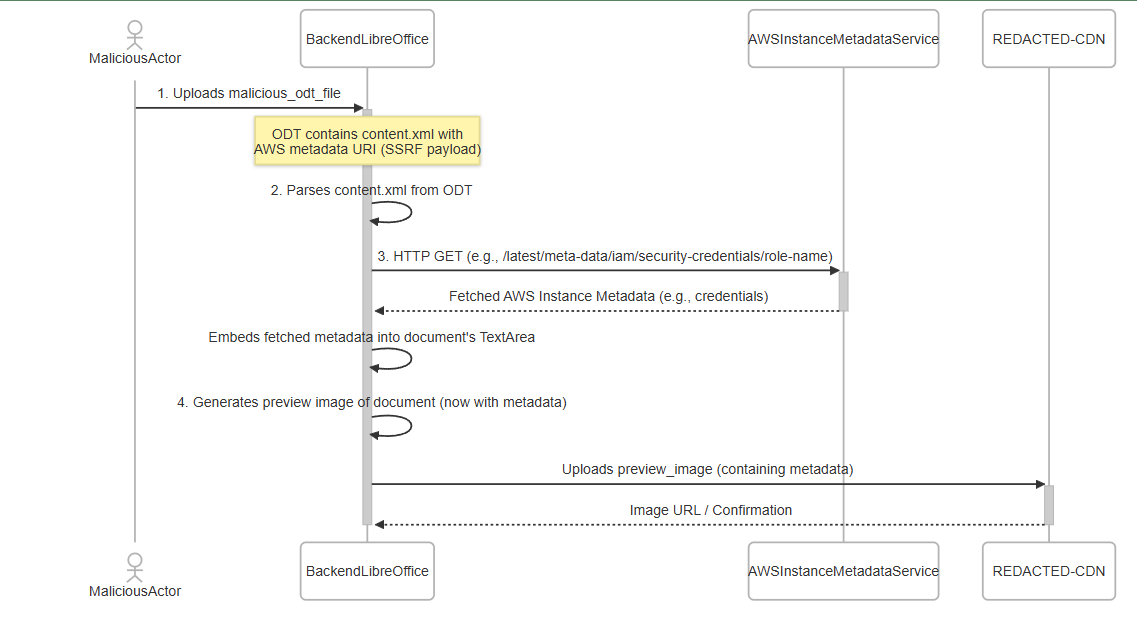
The Entire Attack Flow
This was blind SSRF turned full SSRF with data exfiltration.
If this exploit gave you chills, wait till you see how another multi-cloud setup was breached in How Hackers Exploited REDACTED in a Multi-Cloud Security Breach—a story just as eye-opening.
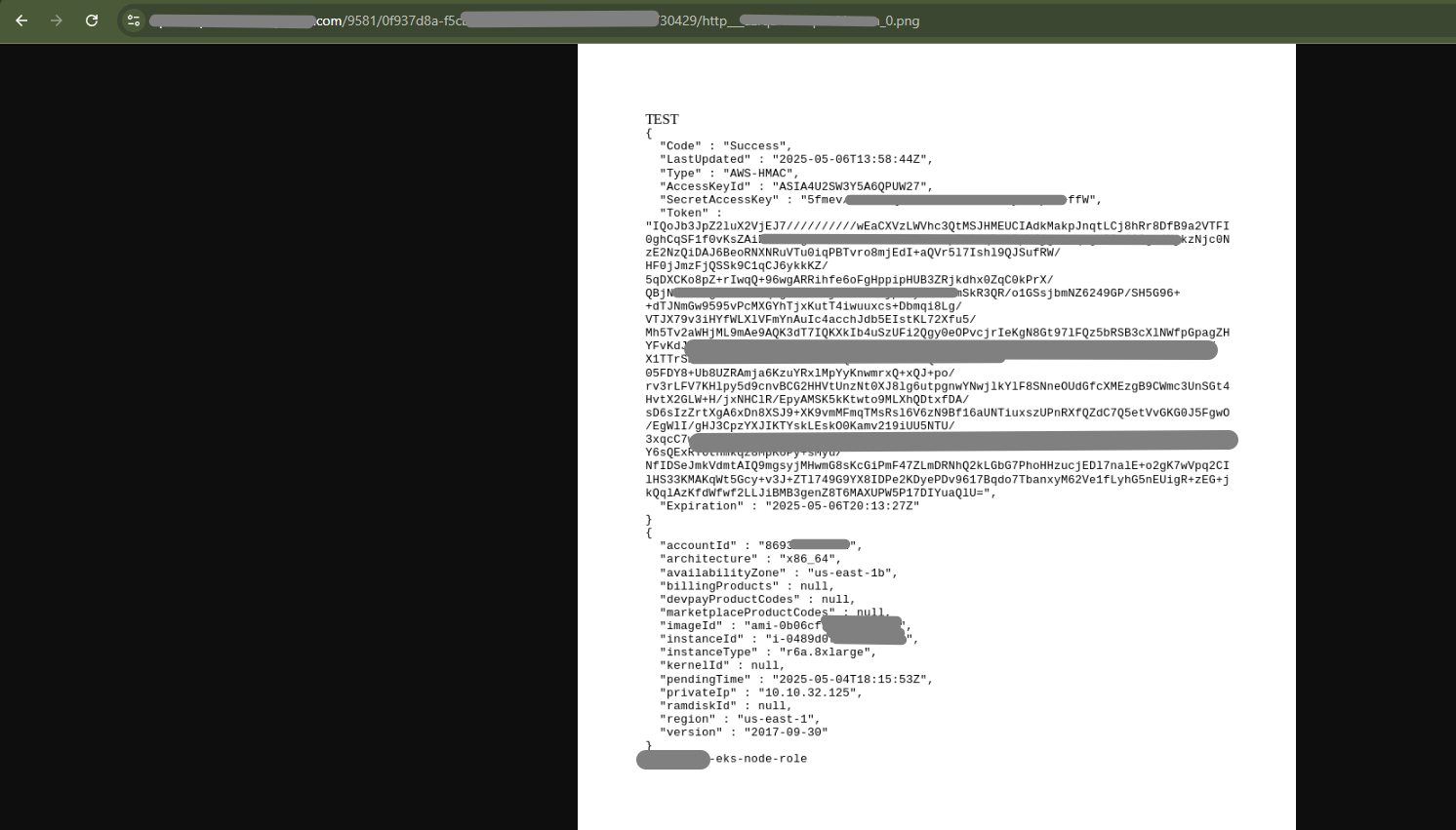
An Attempt to OCR extract the tokens from the image proved to be close to impossible. A little bit of manual intervention was needed to get our hands on the final treasure.
The tokens post extraction gave complete access to AWS Secretmanager revealing close to a 100 secrets across the Organization!
Curious how AWS EC2 metadata services work—or how attackers target them in cloud environments? Start with the essentials in this course:
AWS EC2 and Network Security Basics
This exploit didn’t involve technically super complex chains or obscure bugs. It relied on:
This kind of exploit is exactly what modern threat modeling should catch before code ever reaches production. SecurityReview.ai brings AI-driven threat modeling to your DevSecOps pipeline flagging risks in components like LibreOffice before they become real-world breaches.
These vulnerabilities often exist not because of bad intent—but due to lack of deep cloud security training. Read Top Cloud Security Training Challenges for Large FinTechs to see why even massive teams fall short.
Possible Mitigation given a backend running Java
When loading any ODT document using XComponentLoader.loadComponentFromURL(), we must pass an array of PropertyValue objects that explicitly tells LibreOffice not to update external links.
This would prevent LibreOffice from loading any links. It would not go through the process of updating the doc with any sort of dynamic content.
Specific Property:
Name = "UpdateDocMode"
Value = com.sun.star.document.UpdateDocMode.NO_UPDATE
If you’re building or operating in cloud-native environments, a security review isn’t optional. we45’s Cloud Security Assessment Services help detect chained vulnerabilities like SSRF and insecure file handling before attackers do.
We turned a harmless-looking media upload interface into a powerful SSRF exploit using nothing more than a document file and a well-placed XML attribute. The fact that this worked in such a large-scale platform reinforces a vital truth: security assumptions around third-party software and media processing are often flawed.
So next time your app renders a document or a thumbnail, remember—even pixels can leak secrets.
Want to go beyond just reading about these breaches? Check out Your Ultimate Guide to Multi Cloud Security Training with AppSecEngineer for structured, hands-on cloud security mastery.
AppSecEngineer is your one-stop platform for mastering secure coding, cloud security, and vulnerability exploitation with live labs and real-world attack simulations.

The vulnerability was a Server-Side Request Forgery (SSRF) triggered during document preview generation. A file upload feature allowed attackers to upload malicious .odt files, which were then processed by LibreOffice. This let the attacker force requests to AWS metadata services and extract temporary credentials.
The attack chain worked as follows: Upload .odt file via the “upload by URL” feature. Backend passed it to LibreOffice for thumbnail generation. LibreOffice fetched external resources defined in the document XML. Payloads pointed to 169.254.169.254 (AWS metadata endpoint). Metadata containing AWS credentials was embedded in the generated preview. The CDN hosted the preview, leaking the secrets back to the attacker.
LibreOffice supports dynamic content fetching through xlink:href attributes inside .odt files. This allowed attackers to trick it into fetching internal services. Without restricting document update modes, LibreOffice will blindly follow these links, making it an ideal SSRF vector.
AWS temporary credentials are short-lived access keys provided to workloads (like EC2 instances or EKS nodes). If stolen, they can grant attackers access to: AWS Secrets Manager S3 buckets Internal services Even though temporary, they are powerful enough to escalate into long-term breaches.
The platform used a client-side extension whitelist (assetTypeVsSupportedExtensionsMap). By manipulating request parameters, the attacker uploaded unsupported file types like .html and .odt. Because validation wasn’t enforced server-side, the malicious files slipped through.
SSRF is when an application makes requests to attacker-controlled URLs. In cloud environments, SSRF is especially dangerous because it can access metadata services (169.254.169.254 on AWS), leaking secrets that grant access to cloud resources.
The credentials were embedded inside a thumbnail PNG. OCR struggled with clarity, spacing, and formatting. Manual reconstruction was required to piece together the access keys. This extra step highlights how attackers can stealthily hide sensitive data inside media assets.
Disable external resource fetching in LibreOffice (UpdateDocMode.NO_UPDATE). Enforce server-side file validation for uploads, not just client-side. Isolate document processing in sandboxed environments with no network access. Restrict metadata service access using AWS Instance Metadata Service v2 (IMDSv2). Log and monitor thumbnail generation processes for unusual traffic.
They are increasingly common because many SaaS platforms allow upload by URL and rely on third-party processors like ImageMagick, LibreOffice, or FFmpeg. These processors often fetch external content, creating SSRF opportunities.
This case shows that chained vulnerabilities (file upload + LibreOffice parsing + CDN hosting) can escalate into major breaches. It underscores: Why third-party tools need hardened configurations. How cloud metadata services remain prime SSRF targets. Why security reviews must consider document conversion and media pipelines.


.png)
.png)

Koushik M.
"Exceptional Hands-On Security Learning Platform"

Varunsainadh K.
"Practical Security Training with Real-World Labs"

Gaël Z.
"A new generation platform showing both attacks and remediations"

Nanak S.
"Best resource to learn for appsec and product security"
.svg)




.svg)



.png)
.png)

Koushik M.
"Exceptional Hands-On Security Learning Platform"

Varunsainadh K.
"Practical Security Training with Real-World Labs"

Gaël Z.
"A new generation platform showing both attacks and remediations"

Nanak S.
"Best resource to learn for appsec and product security"


.svg)
.svg)




United States11166 Fairfax Boulevard, 500, Fairfax, VA 22030
APAC
68 Circular Road, #02-01, 049422, Singapore
For Support write to help@appsecengineer.com



.svg)
