Not ready for a demo?
Join us for a live product tour - available every Thursday at 8am PT/11 am ET
Schedule a demo
.svg)
No, I will lose this chance & potential revenue
x
x



Container escape vulnerabilities have reached critical levels in 2025, with high-profile exploits like CVE-2025-23266 (NVIDIAScape) demonstrating how attackers can break free from container isolation with minimal effort. While traditional container security relies on shared kernel boundaries that can be breached, advanced isolation technologies like gVisor and Kata Containers provide robust defense-in-depth protection that can stop even sophisticated escape attempts.
Advanced isolation has now become survival.
What if a single malicious container image breaks free from its sandbox and gains root access to your production Kubernetes cluster in just under 10 minutes? Your customer data, AI models, and business-critical workloads are now at the mercy of an attacker who started with nothing more than a crafted Dockerfile.
Vulnerability Landscape:
A high proportion of these vulnerabilities persist because organizations often rely on legacy base images, may lack fully automated vulnerability scanning in CI/CD pipelines, or inherit risks from upstream images. This “technical debt” keeps risk present even as new threats emerge.
Four critical vulnerabilities in container engine components:
Impact: Wiz data shows 80% of cloud environments vulnerable to CVE-2024-21626
The container software supply chain is a growing target. Attackers embed malicious code or dependencies into trusted base images or exploit weaknesses in open-source components. Notable recent incidents include compromised Docker Hub images and dependency confusion attacks that bypass traditional software supply chain barriers.
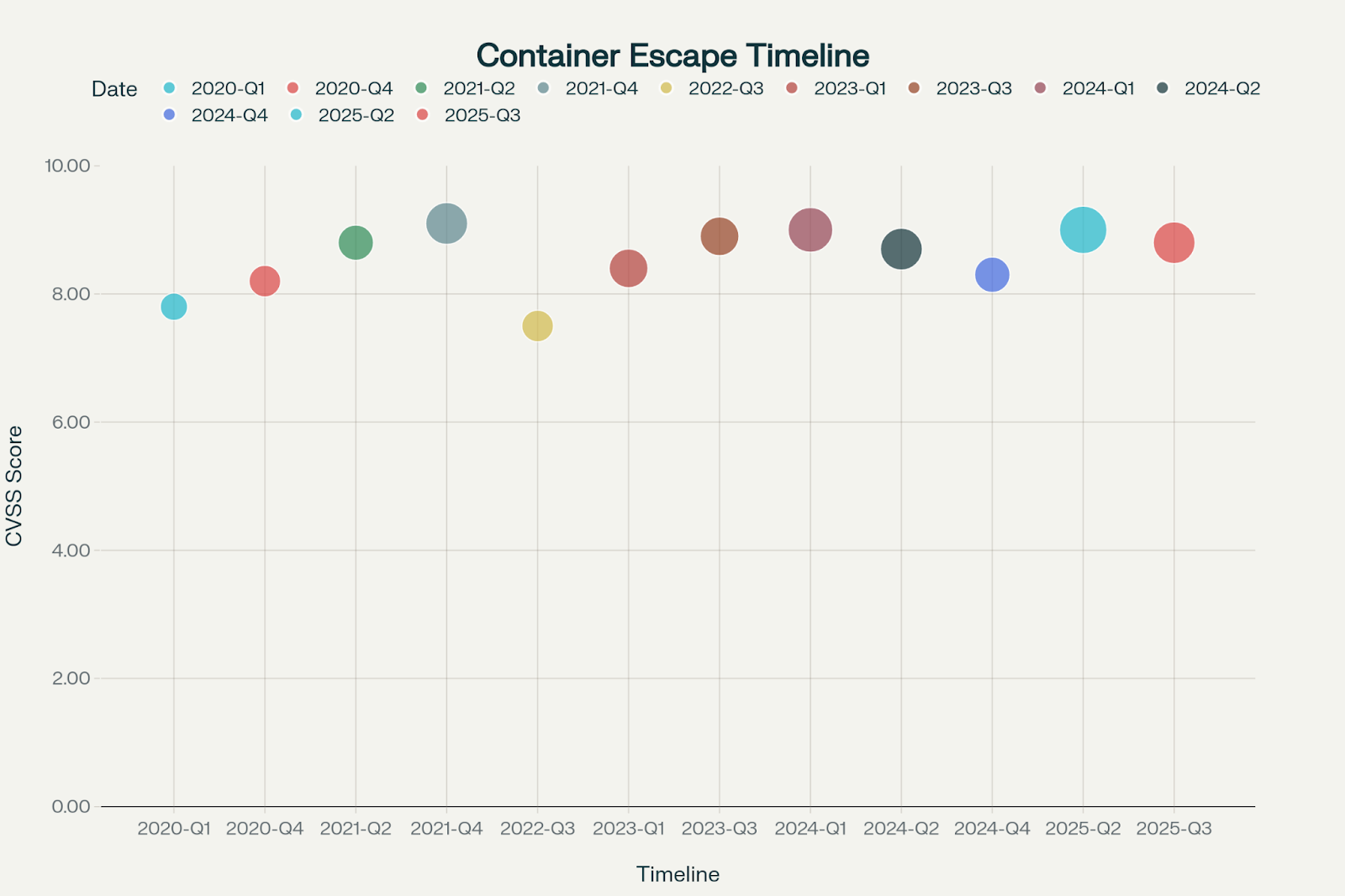
CVE-2025-23266 represents a textbook "Confused Deputy" attack where privileged processes are tricked into executing malicious code:
An attacker could use this vulnerability not just to trigger container escape, but to access sensitive AI model weights, exfiltrate customer datasets, or tamper with cloud infrastructure in minutes. The potential impact ranges from theft of intellectual property to full-blown ransomware outbreaks across the cluster.
Three factors have created a container security apocalypse:
Other recent container escape incidents—such as the runc container breakout and BuildKit privilege escalations—show that the threat is not limited to a single exploit or vendor. Attackers continually probe for new runtime, engine, and config vulnerabilities.
Let me show you exactly how a CVSS 9.0 vulnerability works with just three lines:
Attack Flow:
Immediate Mitigation:
Checklist for Container Security Hygiene:
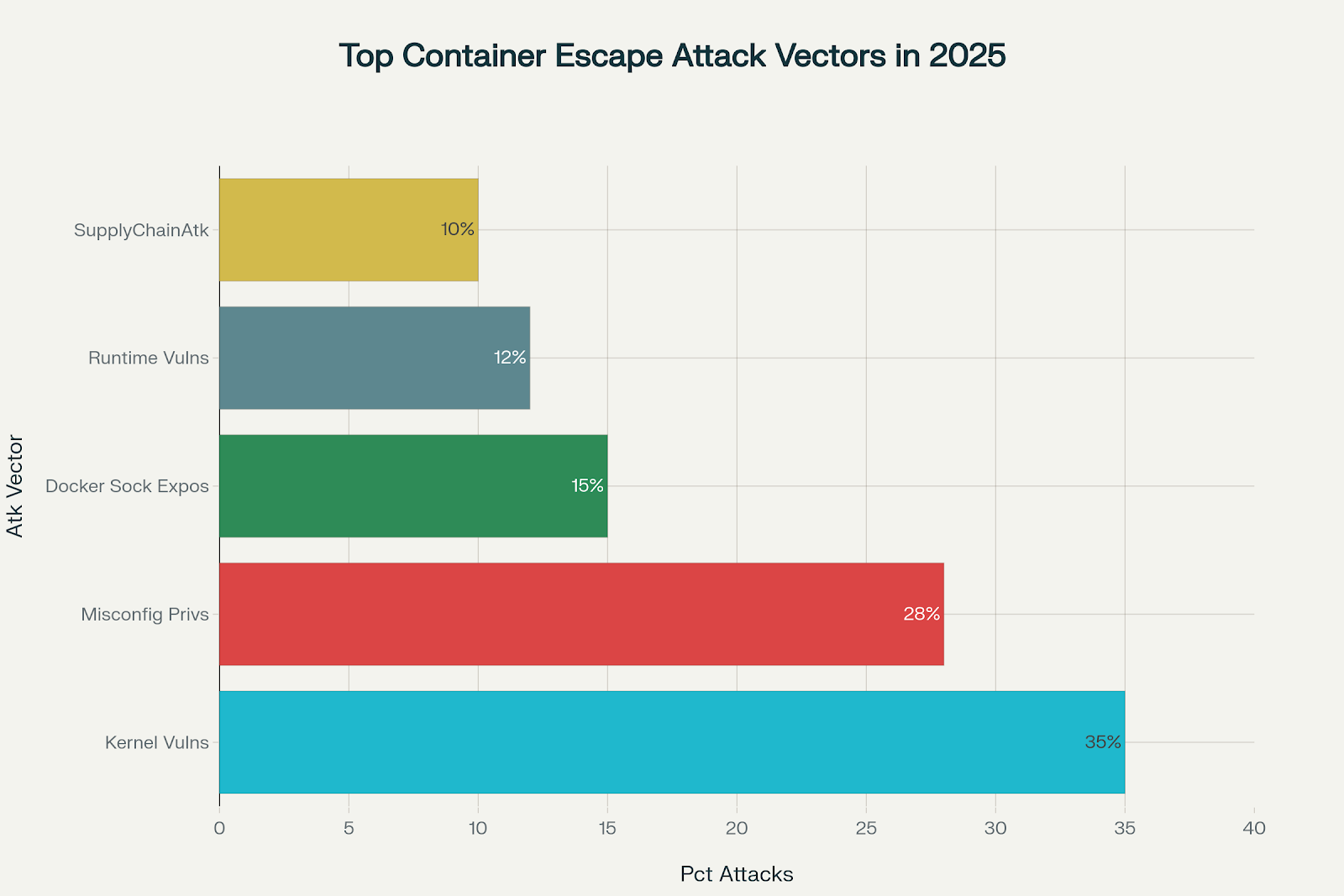
Kernel vulnerabilities and privilege misconfigurations account for 63% of container escapes
Here's the uncomfortable truth: All containers on a host share the same kernel. Linux namespaces, groups, and seccomp filters create the illusion of isolation, but they're just software boundaries that can be broken.
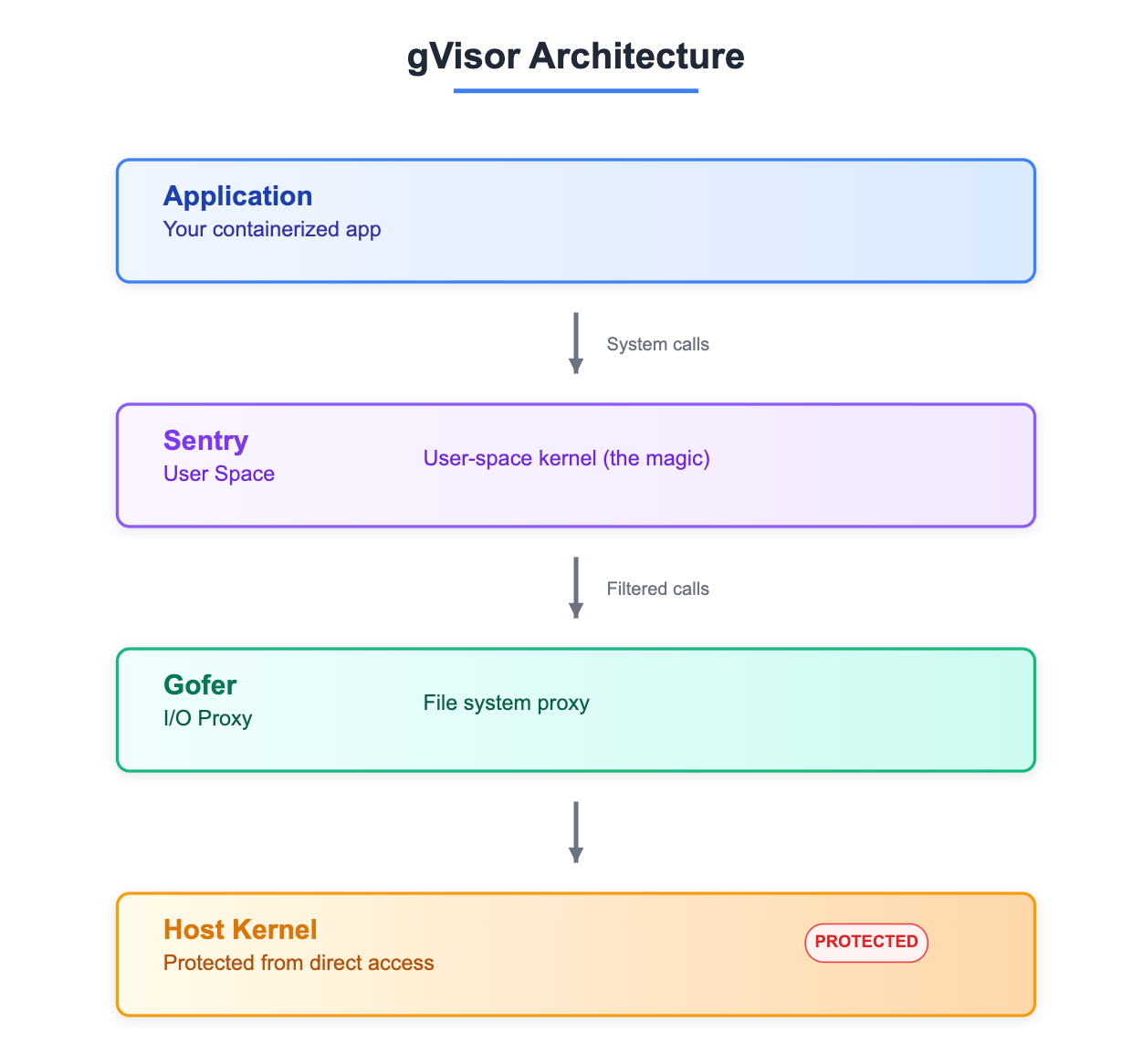
gVisor throws out the rulebook entirely. Instead of trusting the host kernel, it runs a user-space kernel called Sentry that intercepts every system call your application makes.
Kata Containers take a different approach: each container runs in its own lightweight VM with a dedicated guest kernel. Even if attackers escape the container, they're still trapped inside the VM.
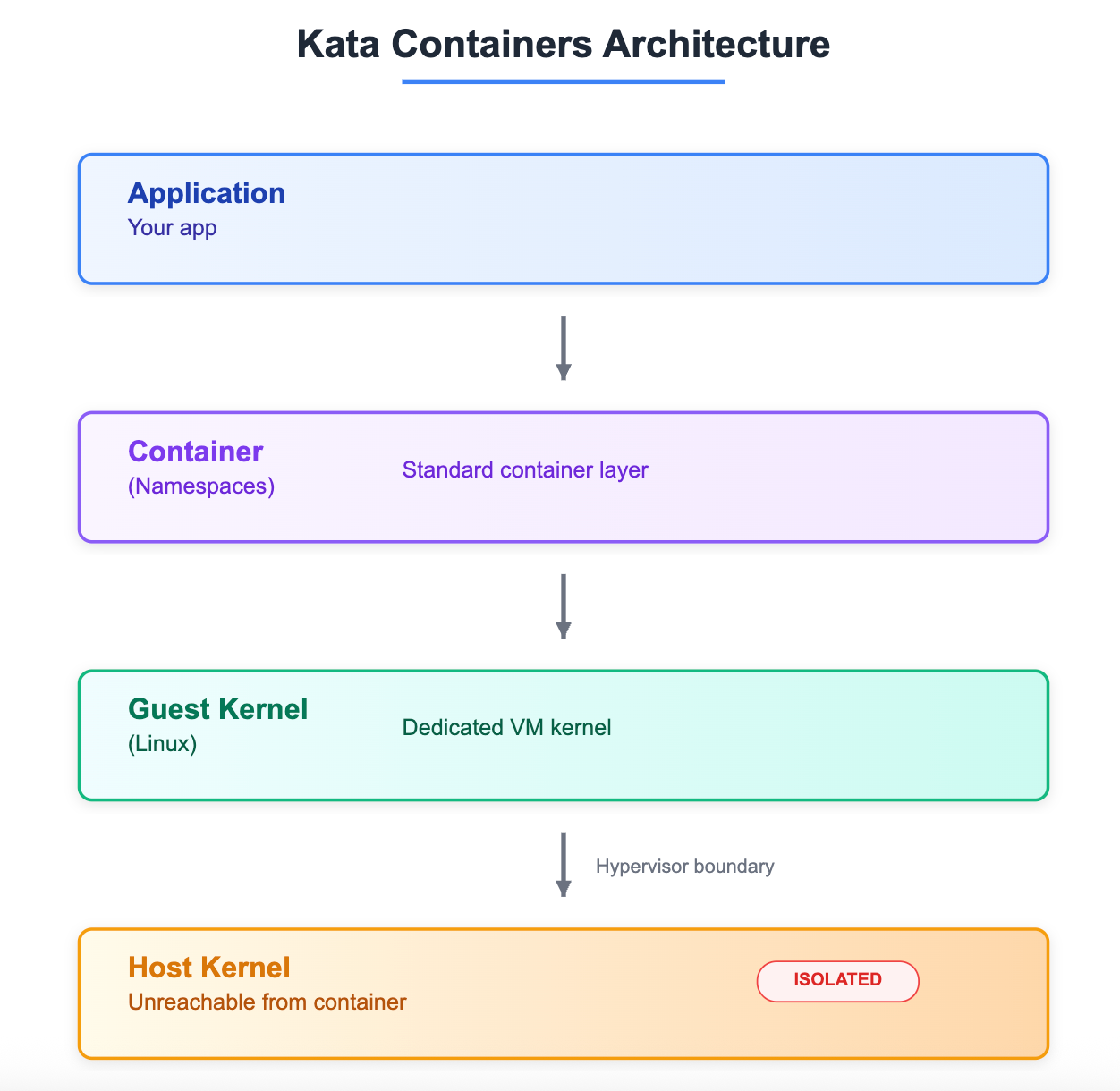
Kata Containers are particularly well-suited for workloads requiring strong cryptographic isolation, such as financial transactions or multi-tenant AI inference, where any exploit impact must remain contained at the VM boundary.
Let's trace through the NVIDIAScape attack against both solutions:

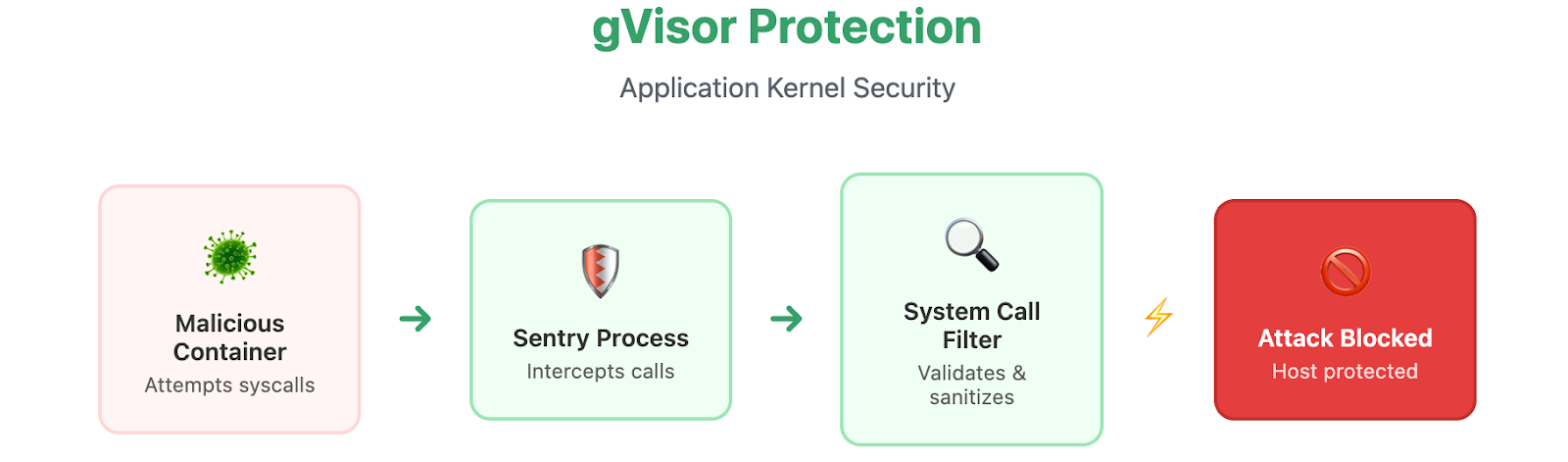
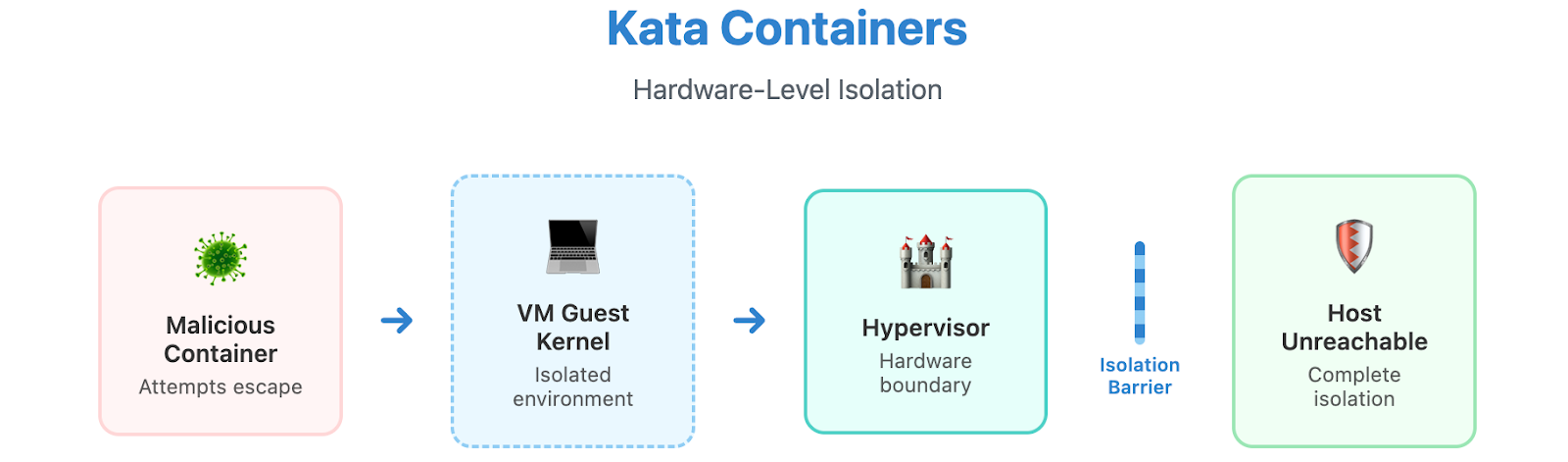
gVisor introduces moderate performance overhead (~10–20%), but offers substantial protection with minimal configuration changes for most apps. Kata Containers provide even stronger isolation at the cost of higher resource usage; however, innovation in lightweight VMMs (like Firecracker) is narrowing this gap. Security-minded organizations often mix both approaches, applying the most stringent runtime only where needed.

Container escapes are happening right now across cloud environments worldwide. The attackers have evolved, their tools have improved, and the stakes have never been higher.
But you're not defenseless.
gVisor and Kata Containers represent battle-tested, production-ready solutions that can stop even the most sophisticated escape attempts. The question isn't whether you can afford to implement advanced isolation - it's whether you can afford not to.
And if you’re interested in deepening your skills, AppSecEngineer offers practical, hands-on training covering container security fundamentals, DevSecOps, and advanced protection techniques for Docker and Kubernetes environments.
The container security war is real, and it's being fought in production environments every day. Make sure you're on the winning side.
.avif)
A container escape is when an attacker exploits a vulnerability in a containerized environment to break out of the container’s isolation boundary and gain access to the host system. This can lead to full control of the host or lateral movement into other sensitive workloads.
Many container images have known vulnerabilities because they often use outdated or unmaintained base images, rely on upstream packages that are not regularly patched, or lack automated security scanning in the CI/CD pipeline. This allows older, unresolved security issues to persist inside production environments.
High or critical severity vulnerabilities are extremely common in production container environments, with studies showing that nearly 87% of container images running in production have at least one high or critical CVE.
Major container escape CVEs include CVE-2024-21626 (runc), which enabled container breakout via a file descriptor leak, and CVE-2025-23266 (“NVIDIAScape”), a high-severity GPU escape attack that exposed 37% of environments running the NVIDIA Container Toolkit to host compromise.
A well-crafted container escape attack can compromise a Kubernetes cluster in under ten minutes, especially when leveraging automated exploits or misconfigured privileges in production.
Common vectors include kernel vulnerabilities, excessive container privileges, exposure of the Docker socket, vulnerable container runtimes, and compromised or malicious base images. Privilege misconfigurations and outdated host or container software also present major risks.
gVisor is a user-space kernel that intercepts and restricts system calls made by containers, drastically reducing the attack surface. By running application workloads with stricter controls, gVisor can block many types of container escape attempts that would exploit the shared host kernel.
Kata Containers runs each container inside its own lightweight virtual machine, with a dedicated guest kernel. This hardware-backed approach ensures that even if a container is compromised, the attacker cannot break out to the host because the VM boundary provides an extra isolation layer.
Yes, container escapes are a significant practical risk, especially for GPU-accelerated AI workloads using tools like the NVIDIA Container Toolkit. Vulnerabilities enabling escapes can expose proprietary models, customer data, or entire cloud clusters if proper isolation and patching are not enforced.
Core best practices include routinely updating and rebuilding images, running containers with the least privileges necessary, scanning for vulnerabilities before deployment, segmenting network access, enabling runtime monitoring, and using hardened isolation solutions for high-risk workloads.


.png)
.png)

Koushik M.
"Exceptional Hands-On Security Learning Platform"

Varunsainadh K.
"Practical Security Training with Real-World Labs"

Gaël Z.
"A new generation platform showing both attacks and remediations"

Nanak S.
"Best resource to learn for appsec and product security"
.svg)




.svg)



.png)
.png)

Koushik M.
"Exceptional Hands-On Security Learning Platform"

Varunsainadh K.
"Practical Security Training with Real-World Labs"

Gaël Z.
"A new generation platform showing both attacks and remediations"

Nanak S.
"Best resource to learn for appsec and product security"


.svg)
.svg)




United States11166 Fairfax Boulevard, 500, Fairfax, VA 22030
APAC
68 Circular Road, #02-01, 049422, Singapore
For Support write to help@appsecengineer.com



.svg)
