Not ready for a demo?
Join us for a live product tour - available every Thursday at 8am PT/11 am ET
Schedule a demo
.svg)
No, I will lose this chance & potential revenue
x
x



For most businesses, establishing clear Application Security (AppSec) objectives is no longer the challenge.
Making security goals part of daily work is where many companies stumble. The result is overlooked risks, expensive fixes, and breaches that harm trust.
Checkmarx’s The Future of AppSec Report 2024 revealed that 92% of organizations had experienced a breach resulting from vulnerabilities in their applications. At the same time, 91% admitted to knowingly releasing applications with known flaws.
IBM’s Cost of a Data Breach Report 2025 reinforces this reality, reporting that the global average cost of a breach has reached $4.44 million, with phishing and stolen credentials remaining among the most common points of entry.
Bridging this gap requires more than policies on paper. Progress depends on people, processes, and technology working together, supported by clear roles, practical training, and tools that integrate into developer workflows.
This blog explores how organizations can turn AppSec goals into consistent execution. It outlines the common challenges that create gaps in implementation and presents strategies for embedding security into development workflows.

Application Security (AppSec) intent refers to the policies, standards, and objectives an organization defines to protect its applications. Its purpose is to spell out what security means for the business, assign responsibility, and keep teams aligned with overall goals.
Examples include:
AppSec implementation refers to the practical application of these policies in everyday workflows. This means weaving security into the software development lifecycle (SDLC), DevOps workflows, and production systems.
A 2024 arXiv study of small and mid-sized businesses reported that 68% had attempted to adopt DevSecOps, yet only 12% conducted security scans on every code commit. The results show how often well-defined goals fail to become consistent practice.
Examples include:
Even with well-defined intentions, many organizations struggle to achieve reliable execution. Several common hurdles make it hard to close this gap:
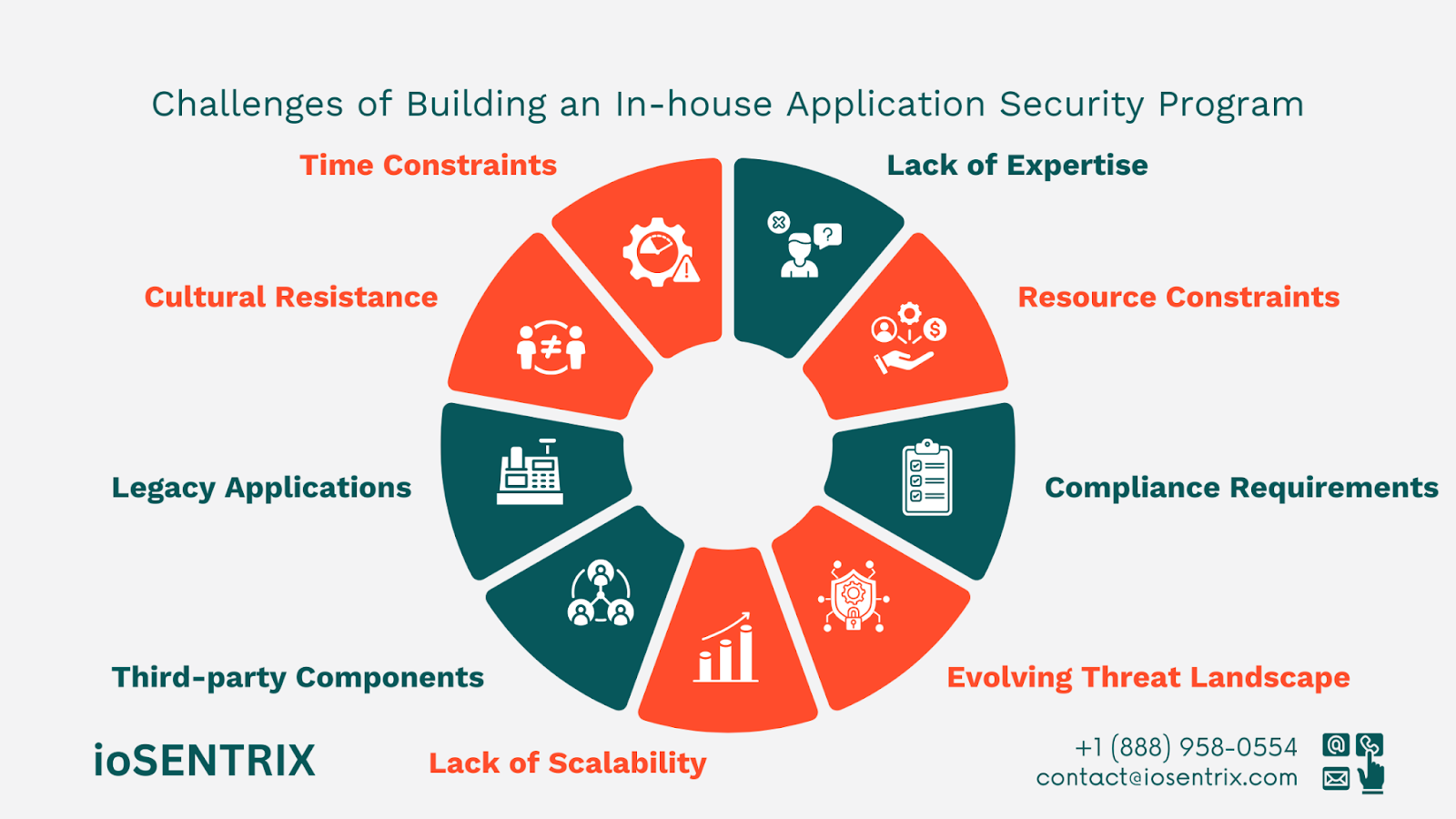
AppSec frequently breaks when culture, inadequate tools, or skill shortages interfere, even with explicit policies.
Development teams frequently believe that security hinders rather than strengthens software. The issue arises when the security, development, and QA groups rarely interact. In the end, checks that should run throughout the project are often pushed to the final stages, where they are least effective.
A study on the arXiv examining small and mid-sized businesses found that 38% of respondents cited cultural resistance as the primary reason AppSec practices fail.
Many teams still tack security on at the last step instead of integrating it into their CI/CD setup. When that happens, issues arise late, and fixing them requires significantly more effort. Manual reviews add another layer of trouble.
They slow projects down, and when the deadline is looming, people sometimes skip them. That’s when weak spots slip through and land in production.
Many teams continue to use tools that are out of step with agile working methods and current designs.
Better solutions are frequently not well incorporated into current workflows, even when they are accessible. Developers become disinterested, and real hazards remain unaddressed if the tools produce a constant stream of false positives or impede development.
The 2025 Application Security Benchmark report from OX Security noted that 95% of security alerts can be safely deprioritized, as most are either duplicates or low risk. This level of noise makes it harder for developers to focus on real issues and undermines confidence in the results, slowing down remediation.
Plenty of developers never get much training in secure coding, so it’s easy to miss problems or fix them the wrong way. At the same time, security teams often struggle to convey risks in terms that leaders can understand.
That gap makes it more challenging to secure executive backing and the necessary resources to close it. This two-sided knowledge gap prevents AppSec intent from becoming a consistent practice.
To close the gap between AppSec goals and actual practice, teams must integrate security into their work, understand how to use it efficiently, and be held accountable through clear checkpoints.
Businesses already employ these tactics frequently, and real-world examples show how effective they are:
Starting security work early in the software lifecycle saves both time and cost. Threat modeling during design provides teams with the opportunity to identify weak points before coding begins. Simple habits, like following the OWASP Top 10, should also be part of routine development work.
The Software Engineering Institute demonstrated the benefits of this approach by incorporating security checks into its CI/CD pipeline before feature development. By treating security as part of the build process from the outset, issues were identified and addressed much earlier.
DevSecOps integrates security into automated pipelines, enabling testing to occur as code moves through CI/CD. Teams can carry out static and dynamic testing, software composition checks, and secret discovery during the process.
The effort does not stop after release. In production, ongoing monitoring and infrastructure as code (IaC) checks help prevent unsafe configurations from reaching users.
A SaaS provider achieved measurable results through this approach:
These outcomes show how automation can enhance both security and delivery performance.
Technology alone cannot close the AppSec gap without skilled teams. Developers need targeted training on secure coding, interpreting test results, and addressing common vulnerabilities.
A security champions program can reinforce this effort by assigning developers within each team to act as advocates and provide peer guidance.
Sage, a global enterprise software company, achieved significant results through this model. The company established a network of over 200 security champions. As a result, it cut the average time to fix vulnerabilities by more than 80%.
To share notes, establish priorities, and maintain project momentum, teams including security, development, and QA must meet often.
Shared KPIs also create accountability, including:
Teams lessen the possibility of recurring problems by integrating incident lessons into automation, training, and coding.
Measurement ensures progress is visible and continuous. Organizations should:
Organizations like Sage show that consistent measurement and adjustment lead to stronger outcomes, with security becoming both reliable and fully integrated into delivery goals.
Teams only stick with AppSec goals when the tools fit into their normal work. If a tool slows things down, it is often overlooked. The right ones save time, reduce manual steps, and still keep projects moving.
Automated testing identifies vulnerabilities as code is created and deployed:
When combined, these techniques significantly enhance coverage and reduce the likelihood that large bugs will make it into production.
Putting security inside the CI/CD pipeline means it runs along with the release, not after it. Teams might add scans during builds, review code with security in mind, or block a release if a serious flaw is still there.
When an app goes live, the job is not finished. Applications in production require constant oversight. Threats don’t wait, so teams need tools that respond right away.
One step alone is not sufficient. However, when combined, they give teams greater visibility and a faster response to issues.
Compliance also needs to be baked into the process. Tools in this area help teams stick to the rules without slowing down development. With policy-as-code, rules can be written, updated, and applied right inside the pipeline. That makes environments more consistent and makes audits easier, since compliance is already built into the workflow.
Strong AppSec depends on both the tech and the culture around it. Teams need guiding principles that shape how security fits into daily work:
From Policy to Practice: Making AppSec Stick
Closing the gap between AppSec intent and actual practice takes more than policy. It calls for early integration, automation where it helps, steady training, teamwork, and regular checks.
Moving forward means setting clear goals, adding security at every stage, and watching progress with useful metrics. Security practices need regular checkups and tweaks.
Application security is integrated into regular software development and operations when handled in this manner.
AppSecEngineer provides teams with practical ways to enhance their security skills through hands-on labs, cloud-based sandboxes, and role-focused training that mirrors real-world development work.
To find out how AppSecEngineer can help your team develop skills and fill security gaps, schedule a demo now!

The AppSec gap is the disconnect between an organization’s security goals and how those goals are carried out in daily work. Many companies set clear policies and standards, but execution breaks down when development teams lack training, tools do not integrate, or security is treated as an afterthought.
Most companies struggle because security and development teams do not collaborate closely, developers lack secure coding skills, and existing tools create noise instead of clarity. Resource constraints and cultural pushback also make security goals difficult to translate into everyday workflows.
Common barriers include poor collaboration between security and development, limited developer training, cultural resistance to security practices, overreliance on compliance instead of risk reduction, and tools that overwhelm developers with false positives.
Organizations can make AppSec work by integrating security early in the development lifecycle, automating checks in CI/CD pipelines, training developers on secure coding, building security champions programs, and setting shared KPIs for security and development teams.
Effective implementation means security is built into design, coding, testing, and deployment. Examples include threat modeling at the design stage, automated security scans during builds, updating vulnerable dependencies, and using runtime protections in production.
Shift left security means moving security practices earlier in the software development lifecycle. By identifying risks during design and coding, teams prevent vulnerabilities from reaching production. This reduces cost, avoids delays, and improves overall resilience.
DevSecOps embeds security into automated pipelines, allowing security tests to run as code moves through CI/CD. This creates consistent checks at every stage and ensures that vulnerabilities are found and fixed before release.
Developers write and maintain most of the code. Without secure coding knowledge, flaws slip through or are fixed incorrectly. Targeted training and security champions inside development teams ensure security practices are practical and consistently applied.
Compliance-driven programs often prioritize ticking boxes instead of addressing actual risks. This results in partial coverage, blind spots, and overconfidence. Real security comes from embedding controls that protect applications, not just passing audits.
Best practices include making security everyone’s responsibility, leaning on automation to reduce manual checks, providing ongoing secure coding training, tracking meaningful metrics, and fostering a culture that treats security as part of quality.


.png)
.png)

Koushik M.
"Exceptional Hands-On Security Learning Platform"

Varunsainadh K.
"Practical Security Training with Real-World Labs"

Gaël Z.
"A new generation platform showing both attacks and remediations"

Nanak S.
"Best resource to learn for appsec and product security"
.svg)




.svg)



.png)
.png)

Koushik M.
"Exceptional Hands-On Security Learning Platform"

Varunsainadh K.
"Practical Security Training with Real-World Labs"

Gaël Z.
"A new generation platform showing both attacks and remediations"

Nanak S.
"Best resource to learn for appsec and product security"


.svg)
.svg)




United States11166 Fairfax Boulevard, 500, Fairfax, VA 22030
APAC
68 Circular Road, #02-01, 049422, Singapore
For Support write to help@appsecengineer.com



.svg)
