Not ready for a demo?
Join us for a live product tour - available every Thursday at 8am PT/11 am ET
Schedule a demo
.svg)
No, I will lose this chance & potential revenue
x
x



Learn how a missing authorization check led to unauthorized access to internal resources and how to fix it with authentication best practices. In this blog post, we delve into a common security incident where a lack of proper authorization checks led to unauthorized users gaining view and edit access to an internal third-party resource. While doing reconnaissance for subdomain enumeration, found one internal subdomain (useful for only internal team tracking purposes) hosted live carrying the upcoming tasks and daily updates for internal employees which was assumed to be secure but found to be more vulnerable. However, the absence of authentication mechanisms allowed anyone with knowledge of the subdomain's URL to access and manipulate the internal content.
The internal subdomain had a static page with daily updates noted in a calendar in which employees could add their daily tasks and embed links for Jira tickets, Figma projects, etc. This security misconfiguration leads to missing authorization checks on the Figma panel. While the panel was located on an internal subdomain, it was not adequately protected by authentication measures.
On visiting all pages in the respective subdomain (calendar.redacted.com) found multiple URLs having Jira tickets for regular updates and tracking which was well secured having SSO from Okta. But there were also project URLs for Figma used for the design and development of the front end across the application. Here, the user needs authentication to view the project having the invite or access from the project admin. Due to a lack of authorization, any user can sign up with their individual credentials and access the project without restrictions. These projects were daily updated and monitored by the internal resources and particularly attackers can make changes on behalf of the organization.
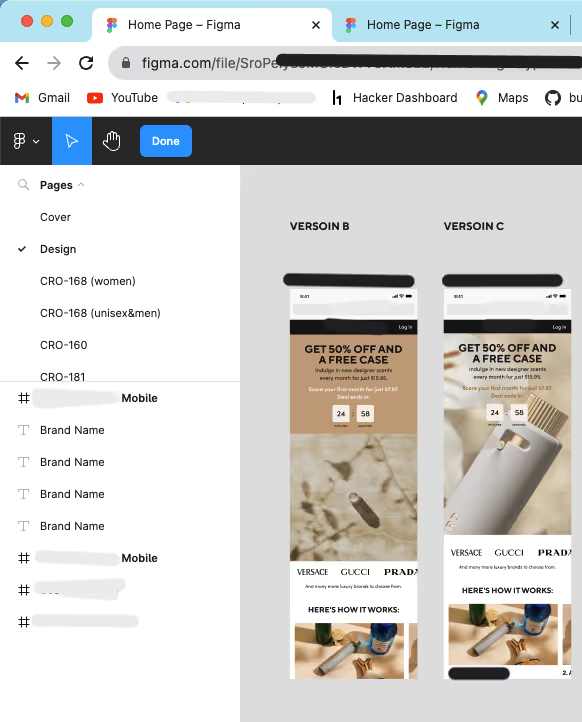
The impact of this security misconfiguration was significant. Unauthorized users could:
To prevent similar unintentional security misconfigurations, it is crucial to implement proper authentication and authorization mechanisms for all internal applications and resources, including those hosted on internal subdomains.

Unauthorized access occurs when individuals gain entry to systems, applications, or data without proper authentication or authorization. This often results from security misconfigurations, weak access controls, or exposed internal resources.
Attackers can exploit misconfigurations, weak authentication mechanisms, or exposed subdomains. Common methods include: • Subdomain enumeration to find unprotected internal resources. • Exploiting missing authentication or authorization controls. • Credential stuffing or brute-force attacks on login portals.
If an internal subdomain lacks proper authentication, unauthorized users can: • View sensitive internal data such as project files, design assets, or customer records. • Modify or delete critical business information. • Inject malicious content that can disrupt operations or compromise security.
Without proper authorization, anyone with access to a URL or system can potentially view, edit, or delete confidential data. This increases the risk of data leaks, compliance violations, and security breaches.
Authentication verifies a user’s identity (e.g., using a password or Single Sign-On). Authorization determines what actions the authenticated user can perform within the system (e.g., read, write, admin privileges).
To mitigate these risks, organizations should: • Implement authentication (e.g., SSO, MFA) to verify user identity. • Enforce role-based access control (RBAC) to limit permissions. • Restrict internal subdomains using VPNs, firewalls, or access control lists (ACLs). • Conduct regular security audits to identify and fix misconfigurations.
SSO simplifies user authentication by allowing access to multiple applications with one set of credentials. When properly configured, it enhances security by reducing password-related vulnerabilities and enabling centralized access control.
You can check for exposure by: • Running subdomain enumeration to detect publicly accessible internal sites. • Performing security audits to identify missing authentication or authorization controls. • Using penetration testing to simulate attacks and uncover vulnerabilities.
• Enable SSO and MFA for authentication. • Set role-based permissions to control who can view or edit data. • Restrict external access using IP allow lists or VPNs. • Regularly audit and update security settings to prevent unauthorized access.
If you find an unprotected internal application: • Restrict access immediately by enforcing authentication and authorization controls. • Review logs to check for any unauthorized access or modifications. • Fix misconfigurations by applying proper security settings. • Conduct a security assessment to ensure no further vulnerabilities exist.


.png)
.png)

Koushik M.
"Exceptional Hands-On Security Learning Platform"

Varunsainadh K.
"Practical Security Training with Real-World Labs"

Gaël Z.
"A new generation platform showing both attacks and remediations"

Nanak S.
"Best resource to learn for appsec and product security"
.svg)




.svg)



.png)
.png)

Koushik M.
"Exceptional Hands-On Security Learning Platform"

Varunsainadh K.
"Practical Security Training with Real-World Labs"

Gaël Z.
"A new generation platform showing both attacks and remediations"

Nanak S.
"Best resource to learn for appsec and product security"


.svg)
.svg)




United States11166 Fairfax Boulevard, 500, Fairfax, VA 22030
APAC
68 Circular Road, #02-01, 049422, Singapore
For Support write to help@appsecengineer.com



.svg)
